

Thinking of a new domain name can be tough, especially when trying to secure the .com and .co.uk extensions. Although …

From the 1st March, Nominet, the registry for all .UK domain names, will be increasing their domain name prices and …
Tags: Domains

If you use Joomla CMS to run your website and haven’t updated it recently then your site is at risk. …
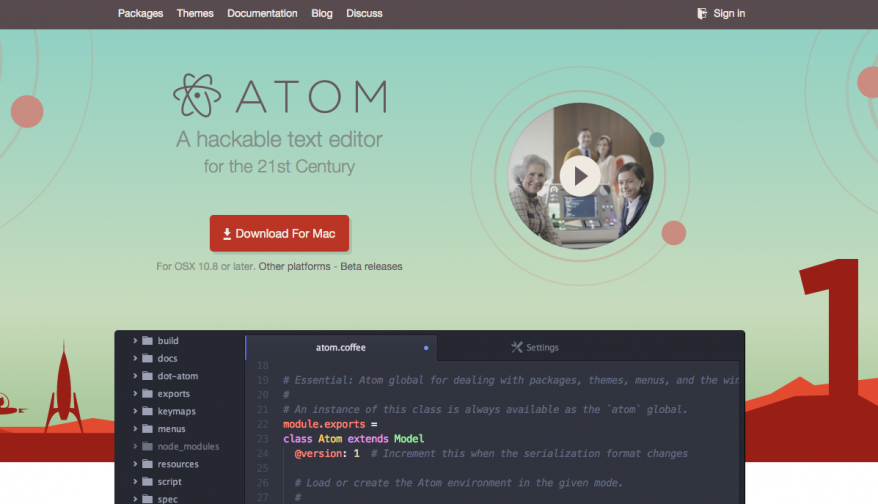
Whether you code HTML, Javascript, PHP, python, etc then you might want to check out Atom “a hackable text editor …

If you use Magento it’s important you apply a patch (SUPEE-5994) to the software as soon as possible. Get patch …

When a visitor clicks on a link that doesn’t work they will often be presented with a dull 404 default …
Tags: development, Hosting

Action required if you use SEO by Yoast A vulnerability has been identified in the SEO by Yoast WordPress plugin …

A vulnerability has been identified in Linux that allows hackers to gain control of systems without the need for any …
Tags: Hosting, vulnerability

A serious Unix vulnerability has been identified called “Shellshock”. This affects all Linux machines and if exploited hackers could gain …

Google announced earlier this month that a small rankings boost would be added to sites that use an SSL certificate …